- Features
- Sequence Diagrams
IPFS Key Vaults
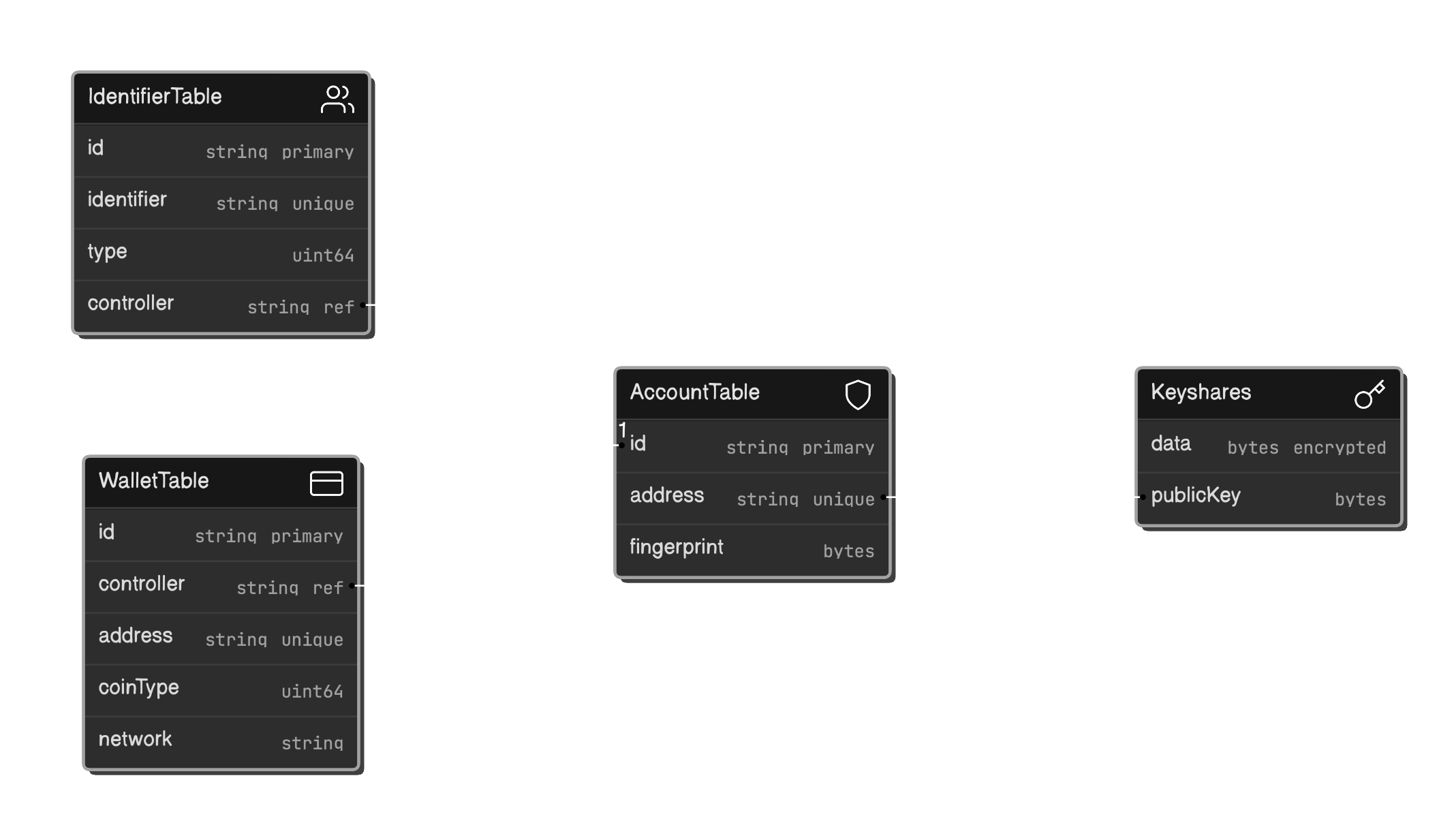
Wallets are stored in IPFS with Encrypted Access available to the User and Sonr Validator nodes.
Multi-Party Computation
Users can authenticate with a simple passkey, removing the need for complex passwords and seed-phrases.
On-Chain Multisigs
Wallets are stored in IPFS with Encrypted Access available to the User and Sonr Validator nodes.
Verifiable Credentials
Users can authenticate with a simple passkey, removing the need for complex passwords and seed-phrases.
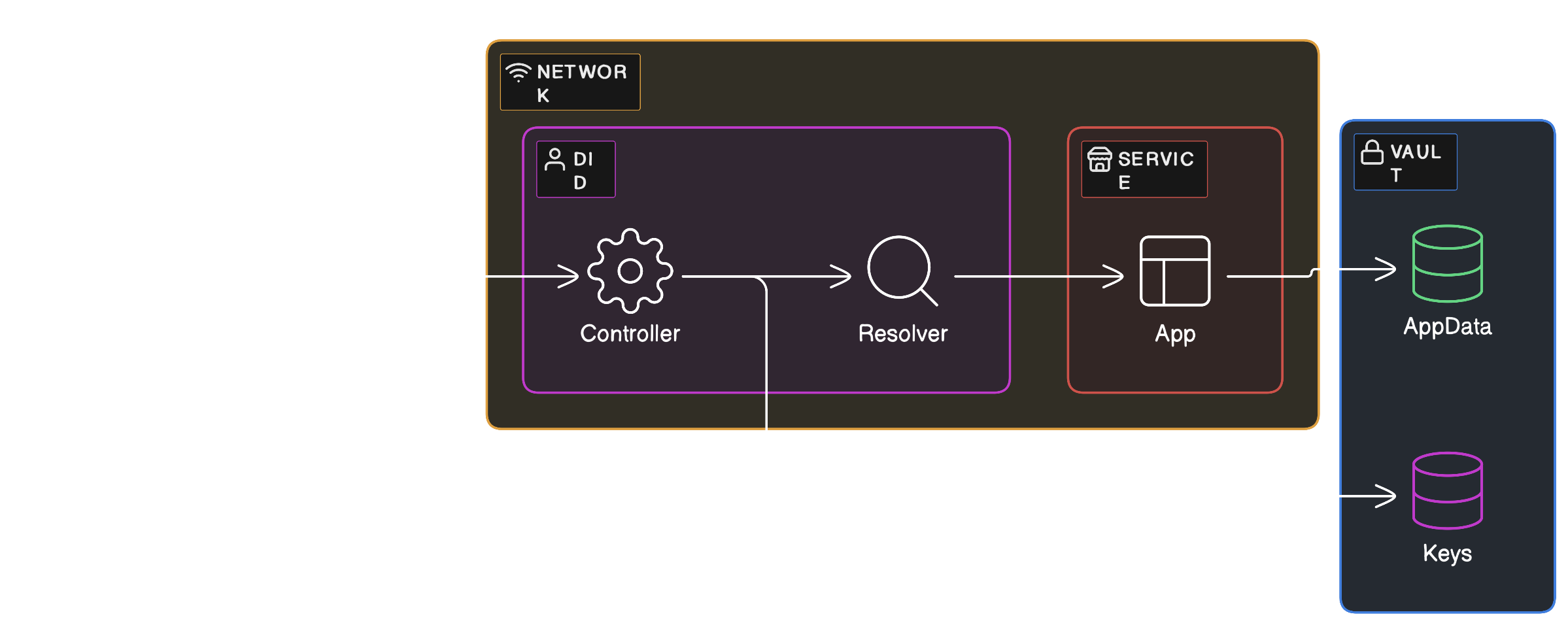
Introducing Decentralized Identifiers (DIDs)
Decentralized Identifiers (DIDs) are a fundamental component of decentralized identity systems. A DID is a unique, globally resolvable identifier that is generated and managed by the identity owner. Unlike traditional identifiers, such as usernames or email addresses, DIDs are not issued by a central authority but are instead created and controlled by the user themselves.The Story of Digital IDs
The Story of Digital IDs
In his original 1989 proposal for what would become the World Wide Web, Tim Berners-Lee outlined a vision of a “universal linked information system” where users would have control over their own data.
He foresaw a decentralized architecture where information would be stored in “nodes” that users could link together through “links” in whatever way made sense to them.
Web1 Identifiers (1990s)
In the early days of the internet known as Web1:
Digital identity was limited and decentralized
People used anonymous usernames or email addresses to identify themselves
There were no widespread standards or protocols for proving one’s identity online
Web2 Identifiers (2000s)
As the internet became more advanced in the Web2 era:
Centralized identity providers emerged like Google, Facebook, Twitter
Single sign-on allowed using one identity across multiple websites
This made identity more convenient but gave control to a few big tech companies
Privacy concerns emerged around tracking and data collection by identity providers
Web3 Identifiers (2010s-Present)
Web3 is ushering in a new phase of digital identity:
Blockchain technology enables decentralized, user-controlled identity
Decentralized identifiers (DIDs) give users more control of their data
Verifiable credentials allow proving claims without oversharing personal info
Self-sovereign identity (SSI) puts users in charge of their identities
But standards are still emerging and adoption is in early stages
The Technical Aspects of DIDs
A DID consists of three main components:- Scheme: The identifier for the DID method, such as “did”.
- Method: The specific DID method used, such as “example”.
- Method-Specific Identifier: A unique identifier within the context of the DID method.
did:example:123456789abcdefghi
Decentralized Identity Methods
DID methods define the specific implementation details for creating, resolving, and managing DIDs on different distributed ledger technologies or decentralized systems. Each DID method has its own specification, which outlines the technical requirements and procedures for working with DIDs within that particular ecosystem.| DID Method | Description |
|---|---|
| did:ethr | Ethereum-based DIDs |
| did:sov | Sovrin-based DIDs |
| did:ion | Identity Overlay Network (ION) DIDs |
| did:web | Web-based DIDs |